The OSI model and Internet Protocol are the foundation on which the digital world—and therefore the cloud—has been built. When we talk about networks, it is easy to think of cables, routers, and servers. Yet, behind every connection lies an invisible architecture that makes communication possible. The OSI model also named ISO/OSI stack and its successor the Internet Protocol Suite, are not simply abstract diagrams.
In this chapter, we will take our first steps into this architecture. The ISO/OSI model, developed as a universal language to describe how information flows across networks, offers a way to interpret the cloud and classify the services it provides. Understanding its layers is like learning the anatomy of digital communication: each level has a specific role, each interaction contributes to the seamless experience of exchanging data.
While the OSI model remains a conceptual framework, the TCP/IP suite—leaner and more pragmatic—has become the actual backbone of the Internet. Together, they represent the theoretical and practical sides of the same story: how humanity has managed to interconnect billions of devices, services, and people.
By exploring these models, we not only gain technical knowledge but also acquire a lens through which we can better understand the cloud-native ecosystems described throughout this book. This journey begins here—with the architecture of communication itself.
Table of Contents
Understanding OSI Model and Internet Protocol Foundation
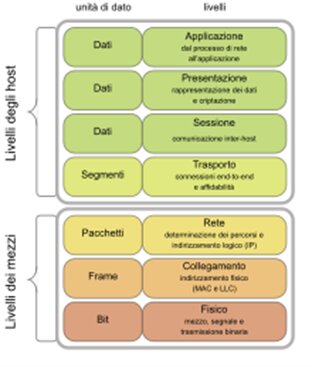
The ISO/OSI stack model can be considered a “tool” for interpreting the cloud and classifying the services offered.
For this reason, we are providing an early description of the reference model.
The ISO/OSI (Open Systems Interconnection) model is a conceptual framework that defines how networks transmit data from sender to receiver (18).
It consists of a stack of protocols that reduce the implementation complexity of a communication system for networking.
The OSI model contains seven layers arranged conceptually from bottom to top.
Below is a brief description of each:
- Physical Layer: This layer handles the transmission and reception of raw, unstructured data from one device to another. It deals with details such as electrical voltage, data transmission speed, etc.
- Data Link Layer: This layer transforms raw bits into structured data frames for transport across the network.
- Network Layer: This layer manages the transport of data from a source to a destination, or more specifically, from one IP address to another.
- Transport Layer: This layer ensures that messages are delivered error-free, in sequence, and without loss or duplication.
- Session Layer: This layer establishes, manages, and terminates connections between local and remote applications.
- Presentation Layer: This layer provides software applications with independence from network operations’ details.
- Application Layer: This layer provides networking services to user applications.
Each layer represents a separate level of abstraction and performs a defined function.
The layers are designed to create internationally standardized protocols.
Each layer corresponds to a specific function within network communication.
We use communication systems daily that adhere to and implement the protocols defined by the ISO/OSI stack.
Over time, the OSI model has effectively been replaced by a simplified version.
The Internet Protocol Suite Based on TCP/IP
The TCP/IP model is a streamlined version of the OSI model. (19)
While the OSI model has seven layers, the TCP/IP model consists of only four.
Here is a brief description of each layer in the TCP/IP model:
- Application Layer: This layer corresponds to the application, presentation, and session layers of the OSI model. It is where data is generated by the user’s application.
- Transport Layer: This layer corresponds to the OSI transport layer. Data is encoded for transmission across the Internet using the UDP or TCP protocol.
- Network Layer: This layer corresponds to the OSI network layer. Data receives a header and a trailer indicating where it should be delivered.
- Network Access Layer: This layer corresponds to the OSI physical and data link layers. The data packet is formatted and prepared for transport and routing through the network.
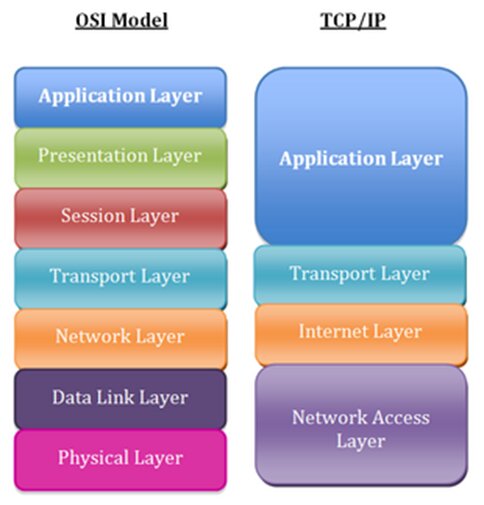
Both models, OSI and TCP/IP, provide data communication services, enabling users to send and receive information from their IP address using services made available by their Internet Service Provider (ISP). However, the TCP/IP model is more practical and is based on standardized protocols, while the OSI model serves as a comprehensive, protocol-independent framework designed to encompass various network communication methods.
The Secure Building: an ISO/OSI metaphor
Understanding the ISO/OSI stack can be challenging for non-technical individuals. This metaphor helps illustrate its structure and importance for security in a relatable way.
Imagine that network communication is like a package that needs to be delivered to a skyscraper with multiple floors. Each floor has a specific function and security mechanisms to ensure that only the correct packages arrive at their destination without being intercepted or tampered with.
Ground Floor – Roads and Physical Access (Physical Layer)
It represents the network of roads and entry doors of the building. If someone cuts the cables or blocks the doors, no package can enter or exit.
Reception – Access Control (Data Link Layer)
Here, incoming packages are checked. If a package has an incorrect label or comes from an unauthorized sender, it is blocked.
Internal Mailroom – Routing Between Floors (Network Layer)
It decides where the package should be delivered inside the building. If the route is incorrect, the package might end up in the wrong place.
Elevators with Controlled Access (Transport Layer)
The elevators transport packages to the correct floors. If an unauthorized person tries to access them, the system blocks them.
Floor Reception – Identification and Authorization (Session Layer)
It controls who can access which rooms and establishes temporary connections between offices.
Office Encryption and Formatting (Presentation Layer)
Here, the packages are opened, and their content is formatted to be readable and secure. If a document is encrypted, the correct key is needed to read it.
Company Departments – Actual Work (Application Layer)
This is the level where data is used by people and business systems, such as email, browsers, or communication apps.
Security Value
Each layer adds a protection mechanism, just like in a well-designed building. If a breach occurs at a lower level, the other levels help mitigate its effects.
If an attacker wants to enter the system, they must bypass multiple barriers, just like a thief trying to break into a well-guarded skyscraper.
Firewalls, encryption, access control, and data management correspond to security measures on the different floors.
Holistic Vision
Looking at the ISO/OSI stack and the Internet Protocol Suite through the lens of cloud-native ecosystems allows us to see beyond mere technicality. These models are not just diagrams in textbooks — they are living architectures that still shape how we design, secure, and evolve digital infrastructures.
Each layer, whether physical or logical, represents both a boundary and an opportunity: a boundary that protects data integrity, and an opportunity to innovate by building new services on top of stable foundations. The transition from the conceptual OSI model to the pragmatic TCP/IP suite reflects the continuous dialogue between theory and practice, vision and implementation.
In the broader context of cloud-native ecosystems, understanding protocols means understanding trust, resilience, and scalability. Protocols are the silent contracts that allow billions of interactions to occur every second, enabling businesses, communities, and individuals to connect and thrive.
By exploring these frameworks holistically, we can appreciate how the invisible scaffolding of communication — from copper wires to encrypted packets — underpins not only today’s Internet but also the evolving landscape of cloud-native services. And just as every archway opens into a wider landscape, so too does this knowledge open the path toward innovation, security, and sustainable growth in the digital era.
References
This article is an excerpt from the book
Cloud-Native Ecosystems
A Living Link — Technology, Organization, and Innovation